“Left unmatched, and with no reasonable workaround, devices
are exposed right out of the box. OEMs also cannot revoke the valid signed
vulnerable components, making unmatched versions valid for installation on
devices”
Statement by Check
Point Software Technologies on the Certifi-gate vulnerability
Google Android just isn't having a great Summer of 2015.
Now another vulnerability has reared its ugly head in the
form of Certifi-gate whose discovery was announced on Thursday August 6th
2015 by Researchers at Tel Aviv-based company Check Point Software Technologies as
described in the article “Android
flaw lets hackers spy on you with your own phone”, published August 6, 2015
by AMANDA SCHUPAK Amanda Schupak, CBS News.
 |
If you read my blog article on the StageFright Vulnerability
entitled “Security
Firm Zimperium reveals StageFright Bug - Why Automated Video Playback in
@Google @Android is a Hacker's Thermonuclear War” you may have thought,
what could possibly be worse than a security glitch that affect 82% of all
smartphones?
Try the Certifi-gate vulnerability!
According to Israeli researchers Ohad Bobrov and Avi Bashan,
the newly minted vulnerability affects the remaining 18% of Google Android 5.0
Lollipop smartphones by hijacking security certificates as reported in the
article “Vulnerability
Warning: There's Another Way To Hack Hundreds Of Millions Of Androids With One
Text”, publishing AUG 6, 2015 by Thomas Fox-Brewster, Forbes.
So how does this security vulnerability work? Believe it or
not, it's as simple as calling Customer Care for Remote Assistance!
Check Point
Software Technologies discover Certifi-gate – How to Remotely Control an
Android smartphone
Revealed at Black Hat Conference in Las Vegas on Thursday
August 6th 2015, the Certifi-gate vulnerability affects all versions
of Google Android.
But more worryingly, it affect Google Android 5.0 Lollipop,
which was thought to be more secure and still hasn't achieved 18.1% of Android
Devices as reported in the article “iOS
8 hits 85% adoption rate; Android Lollipop only at 18%”, published August
5, 2015 by Lance Whitney, CNET News and “Android
Lollipop slowly nears 20 percent mark after eight months of release”,
published Aug 5, 2015 By Tasneem Akolawala, BGR.
 |
The Certifi-gate vulnerability takes advantage of preloaded Apps
called Remote Support Tool (mRST) Apps and system-level plugins that allow
mobile carriers and manufacturers to remotely access your phone to troubleshoot
problems as described in the article “Check
Point: Certifi-Gate-based attacks could take complete control of Android
devices”, published August 6, 2015 By Steven J. Vaughan-Nichols, ZDNet.
They are typically used by Customer Care Agents to remotely
fix problems on your smartphone. Hint: they are also used by CSA (Call Center
Agents) here in Jamaica to remotely diagnose smartphones, so it’s well known!
These Apps are the Smartphone version of remote Desktop Apps
like Google Chrome Remote Desktop that allows you to remotely access your
desktop via your Google Chrome Browser as described in my Geezam blog article entitled “Google
Chrome Remote Desktop lets you control your Computer from Google Chrome for
Android App”.
Hackers, knowing about how these mobile Remote Support Tool
(mRST) apps work, can easily duplicate the supposedly secure authentication
certificates. Thus hackers can use this vulnerability to gain access to your
smartphone.
They can do this by simply designing an App that targets the weakness, giving them remote access to any and every Google Android Smartphone that downloaded a malicious third-party App similar to the ones described in my Geezam blog article entitled “Google Play Store Apps with AdWare threat to Android Security”.
Lollipop
vulnerable to Certif-gate – Why monthly updates cannot work against
fragmentation
So, this means that all current Google Android 5.0 Lollipop
are vulnerable in what is potentially a more serious security flaw that
StageFright.
This as the security vulnerability takes advantage of the
certificates that provide the privileged permissions as noted in the article “Certifi-Gate:
Massive Android vulnerability affects hundreds of millions of smartphones and
tablets”, published August 6, 2015 By David Gilbert, International Business Times.
 |
Android cannot revoke them, as they're built into Android
and thus can be exploited by developers of third-party apps from Third-party
App Stores and even apps sold from the Official Google Play Store.
Google, after the shock of StageFright, in collaboration
with Samsung, LG, Sony and ZTE, has promised monthly bug fixes as soon as
Google starts sending them out as stated in the article “Stagefright
shocks Samsung, LG, and Google into taking phone security seriously”
published August 7, 2015 By Andy Boxall, DigitalTrends.
Still, that's unlikely, thanks to the competitive nature of
the smartphone world and the reluctance of Carriers and smartphone makers to
work together to update every Android smartphone.
This is true especially if they're not selling, which may be
due to competitive forces and hence the reluctance to work together as explained
in the article “Why
a billion Android phones will never be safe”, published August 7, 2015 by Jeffrey
Van Camp, DigitalTrends and “Waiting
for Android’s inevitable security Armageddon”, published Aug 6, 2015 by Ron
Amadeo, ARS Technica.
According to OpenSignal, an App that gauges mobile signals,
there are some 24,093 different Android devices made by 1,294 companies in 2015
as reported in the article “Android
fragmentation: There are now 24,000 devices from 1,300 brands”, published
August 6, 2015 By Liam Tung, ZDNet.
So working together may be the only way to protect innocent
Android users from becoming slaves to a remote Botnet, Guardians of the Galaxy
Style!
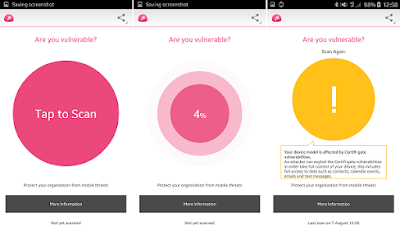
As a way of providing assistance, Check Point Software
Technologies has created Certifi-gate
Scanner App that's available in the Google Play Store that allows users to
assess their Smartphone to see if they’re vulnerable to the Certifi-gate.
Hopefully Google and pals get their act together before a
super hacker launches a first strike, Tsar Bomba Style!
Here's the link:
Check Point
Software Technologies Twitter Feed: @checkpointsw
No comments:
Post a Comment